Set Up a Kali Linux VM
Register / Sign In
Connect to the VPN
Choose a Lab Machine to Hack
Hack a Challenge
Find the Flags
Set Up a Kali Linux VM
Kali is a Linux distribution based on Debian, maintained by Offensive Security, that comes with numerous penetration testing software packages pre-installed.
While not a requirement — you can hack boxes from almost any platform — it will allow you to spend less time downloading and installing software. It is also good practice to keep your box hacking / penetration testing activities at least somewhat isolated from systems you use for other purposes.
Install VM Software and Kali Linux
- Download VMWare (recommended — Workstation Player for Windows & Linux and Fusion Player for MacOS are free) or Virtualbox.
- Download a Kali Linux image for whichever platform you will use. The Kali download page also has options for other platforms & formats (ISO, live boot, container, cloud, etc.) if you prefer.
- Follow the Kali Guest VM installation guide for VMWare or VirtualBox.
- If you have difficulty getting a Kali VM to run properly, other options are Kali Live Boot on a CD/DVD/USB or HtB “Pwnbox”.
Register / Sign In
HtB is free to use and offers a number of “hackable”, or intentionally vulnerable, virtual systems. There is a Getting Started guide on the HtB help site if you find yourself in need of additional guidance beyond what is provided here.
- Go to https://www.hackthebox.eu
- Sign in if you already have an account
OR
Click “Join Now” and register
(“Skip Onboarding” will get you past the demographic questions)  Once logged in, you will see the HtB Dashboard, which you can always return to by clicking “Home” at the top of the left-side toolbar.
Once logged in, you will see the HtB Dashboard, which you can always return to by clicking “Home” at the top of the left-side toolbar.- Basic HtB is free. The “VIP” and “VIP+” subscription levels give you VPN and machine instances with fewer (or no) other users as well as access to all of the retired machines and challenges, and some additional hacking adventures.
- HtB also offers “Pwnbox“, a hosted Parrot linux instance with web-based desktop access. Free tier includes 2 hours per month, 24 hours/month for VIP, and unlimited for VIP+.
Connect to the VPN
If you prefer to use Pwnbox, see the HtB Help to access your Pwnbox and and skip to Choose a Lab Machine to Hack below. A VPN connection is not required to Hack A Challenge.
- At the top right on the HtB Dashboard, click the “Connect to HtB” button
- Click “Machines”, then “OpenVPN”
- Click “VPN Access” and select “US-Free”
- Click “VPN Server” and select whichever has the fewest users (the blue number)
- Wait until the “Download VPN” button lights up green and then click on it. This will start a download of your OpenVPN configuration file.
- From your box-hacking system or VM (kali recommended but not required), start the OpenVPN client with the .ovpn file you just downloaded, or from the (linux) command line:
openvpn --config <file_you_downloaded>.ovpn
You can add the --daemon option to have it run as a daemon (background system process) - The OpenVPN GUI, or ifconfig from the (linux) command line, will show your private IP address for the HtB VPN connection. It is also shown if you click into “Lab Access” on the HtB Dashboard once you have connected. You will need this address if you use a reverse shell or similar while hacking!
- If you find your VPN connection or the machine you’re hacking very slow, you can try a different server or access region. You will have to download a new .ovpn file and reconnect if you do this.
Choose a Lab Machine to Hack
(If you would like to try a Challenge instead, those are covered in the next section)
- From the HtB Dashboard, click on the “Labs” button in the left-side toolbar, then click “Machines”
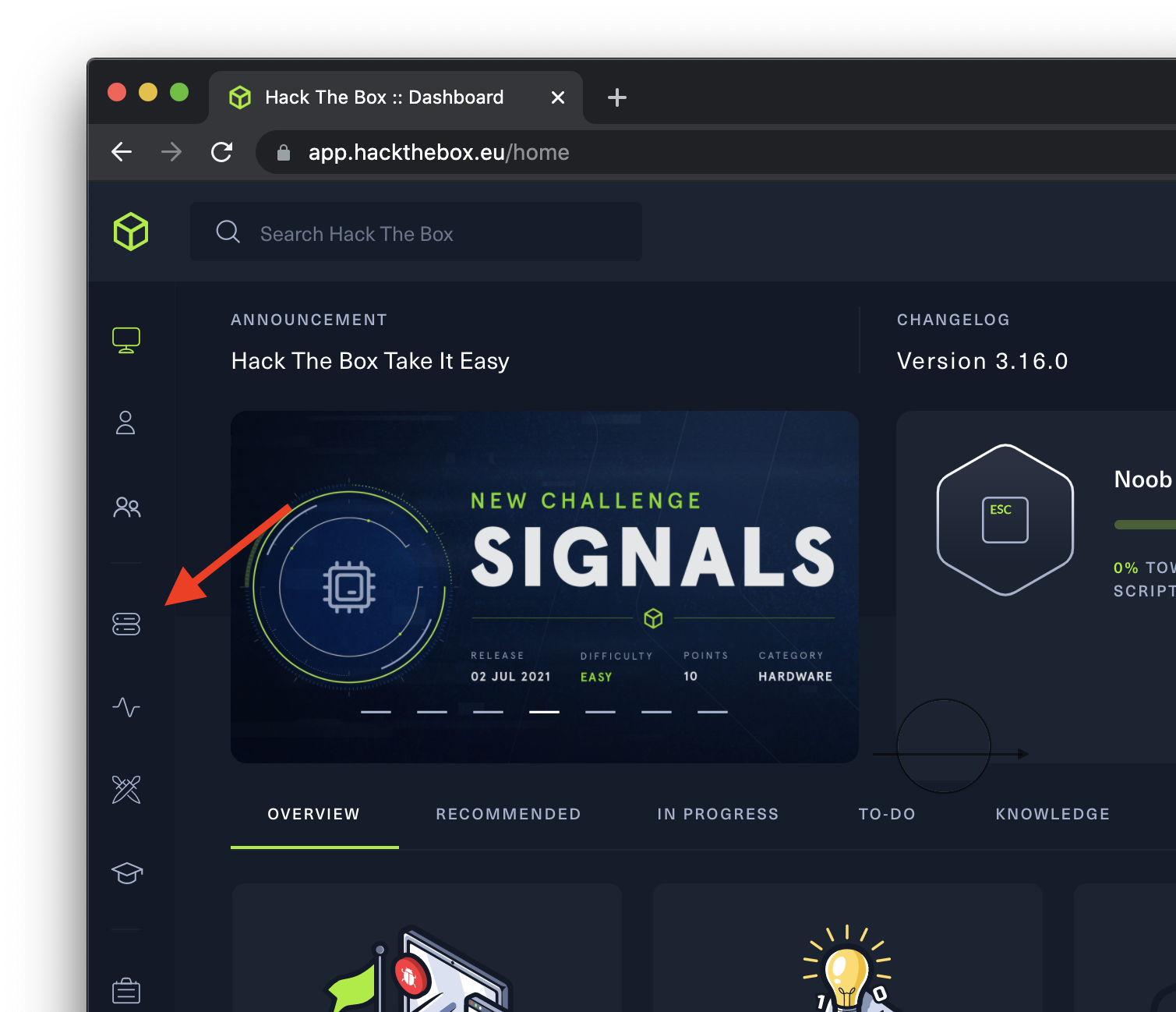
- Machines are arranged by difficulty, Easy through Insane. There is also a “User Rating” indicator, which you can use as an additional gauge of how difficult HtB users found the machine to be.
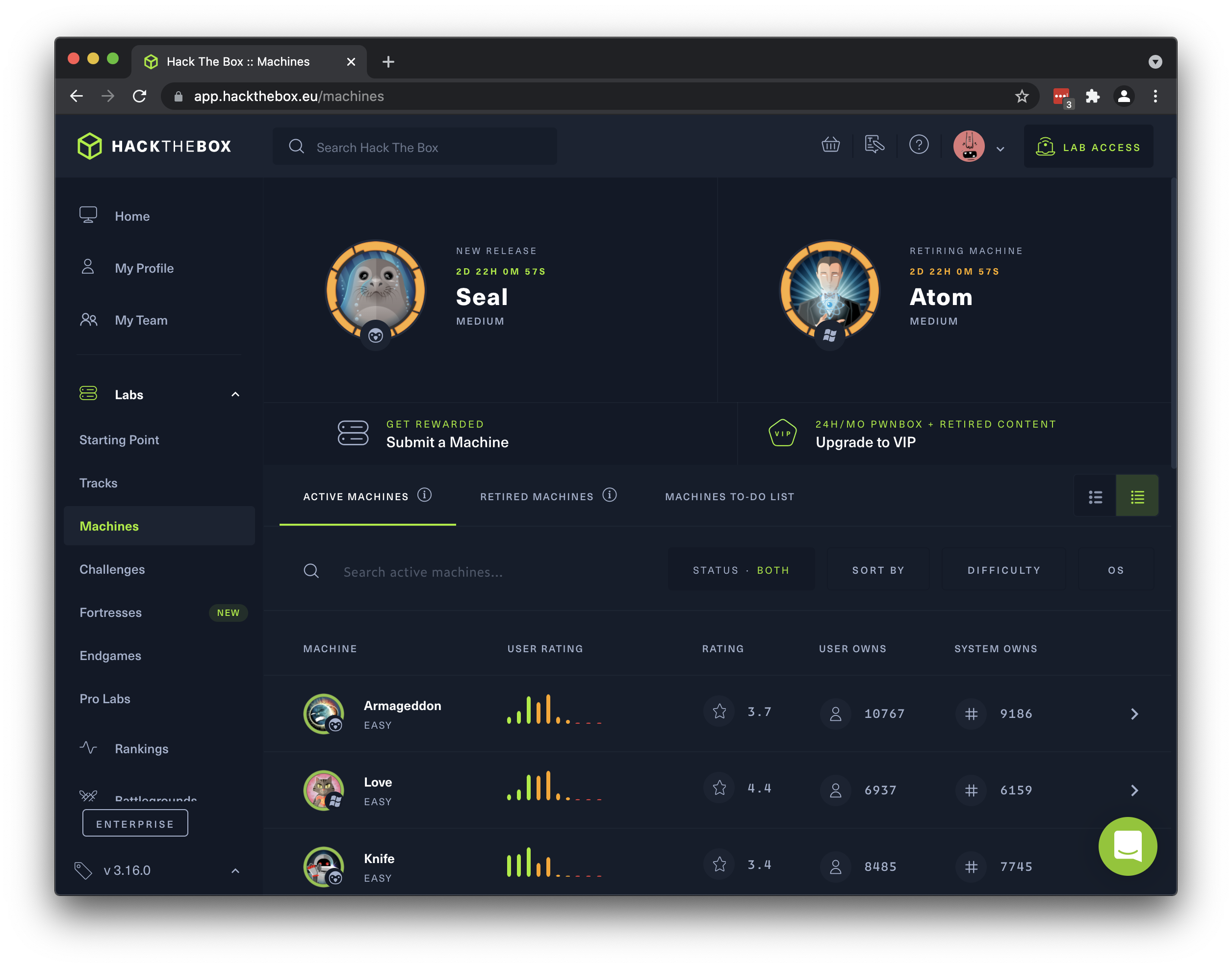
- Select a machine and click its name, then click “Join Machine” (“Spawn Machine” for paid users) on the left side of the page, under the machine name. You can only have one active machine at a time, so if you want to switch machines you will first have to leave the currently active one.
- Once you have joined or spawned the machine, you will see its IP address displayed in the left column of the machine detail page.
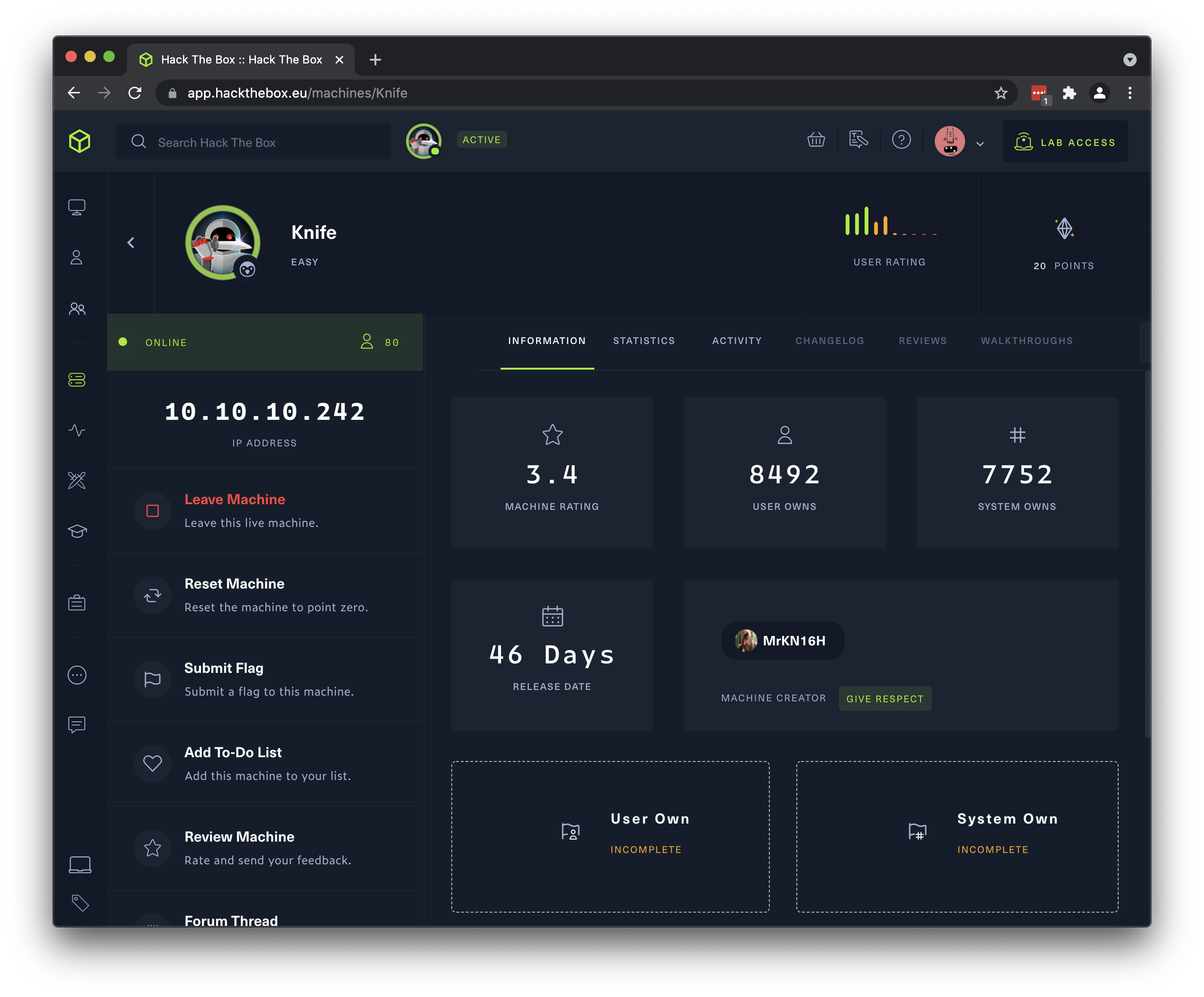
- It’s a good idea to create a directory on your hacking system for each machine, to keep notes, command output, scripts you modify for this box, etc. all in one place.
- Start hacking!
A good place to begin is with an nmap command, such as:
nmap -T5 -A -v -sV -Pn -oN nmap-scan -p - 10.10.10.X
replacing 10.10.10.X with the IP address of the box you’re hacking
This will leave a file called nmap-scan in your current directory with some valuable information about the open ports on your target. You can find look up the rest of the nmap command line options if you’re curious. - Not sure what machine to hack first? Try the Starting Point lab for some “Very Easy” warmup machines. A little googling might even find you some walkthroughs for these if you’re really stuck.
- Other resources for self-paced learning:
- Hack the Box Academy: https://academy.hackthebox.eu
You get 30 “cubes” when you sign up, modules cost 10, 100, 500, or 1000 cubes (50 cubes = $5, discount for subscription plans), you get some cubes back as you complete exercises.
Suggested modules: Setting Up and Getting Started - TryHackMe: https://tryhackme.com
Free & subscription tiers, offensive & defensive topics
Suggested module: Basic Computer Exploitation - OverTheWire: https://overthewire.org/wargames
Free, bite-size security games from the command line - (BHS employees: see CDG SharePoint for past Lightning Talks on related topics)
- Hack the Box Academy: https://academy.hackthebox.eu
- See Find The Flags below for information about what you’re looking for and what to do once you find it.
Hack a Challenge
Challenges are categorized, bite-sized hacking puzzles similar to problems you’d encounter in a Capture the Flag competition.
- From the HtB Dashboard, click on the “Labs” button in the left-side toolbar, then click “Challenges”
- Challenges are grouped into categories:
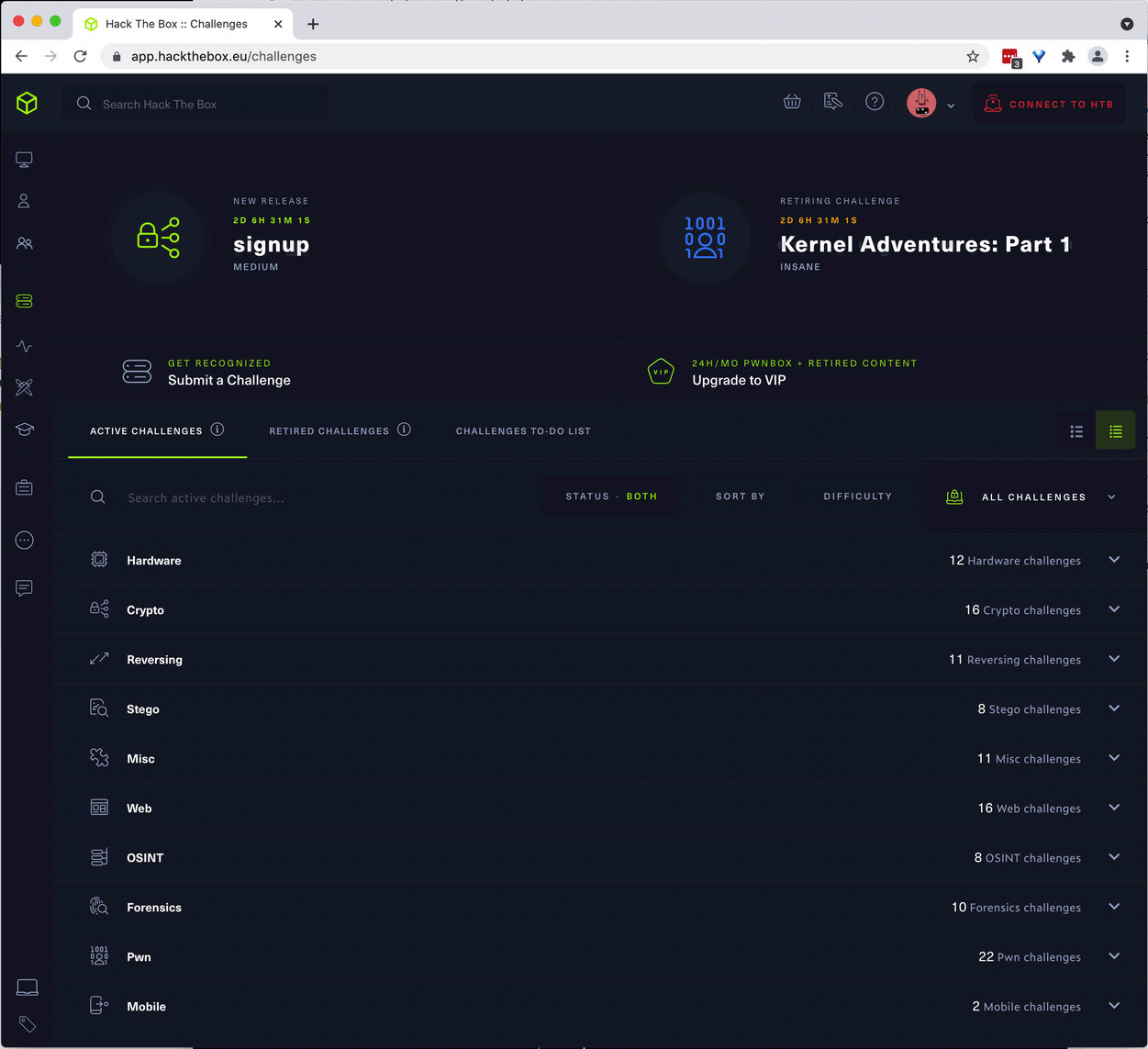
- Hardware – hack different hardware platforms
- Crypto – decipher cryptographically-encoded data
- Reversing – reverse engineer a program to figure out how it gets to the flag
- Stego – find a flag hidden in some ordinary-looking data, like an image, using steganographic techniques
- Misc – things that don’t fit into any of the other categories
- Web – find and exploit a vulnerability in a web-based application
- OSINT (Open Source INTelligence) – use publicly-available information to track down the flag
- Forensics – locate a flag hidden in a network traffic dump, disk image, or other type of data that might be recovered from a compromised system
- Pwn – exploit a binary using memory corruption techniques in order to reveal the flag
- Mobile – find a flag hidden in mobile device apps and/or data
- Click on a category to expand its list of Challenges. Within a category, each Challenge has an assigned difficulty level and a user difficulty rating, just like machines.
- Click on a Challenge to see details, download necessary files, and activate an online instance if necessary.
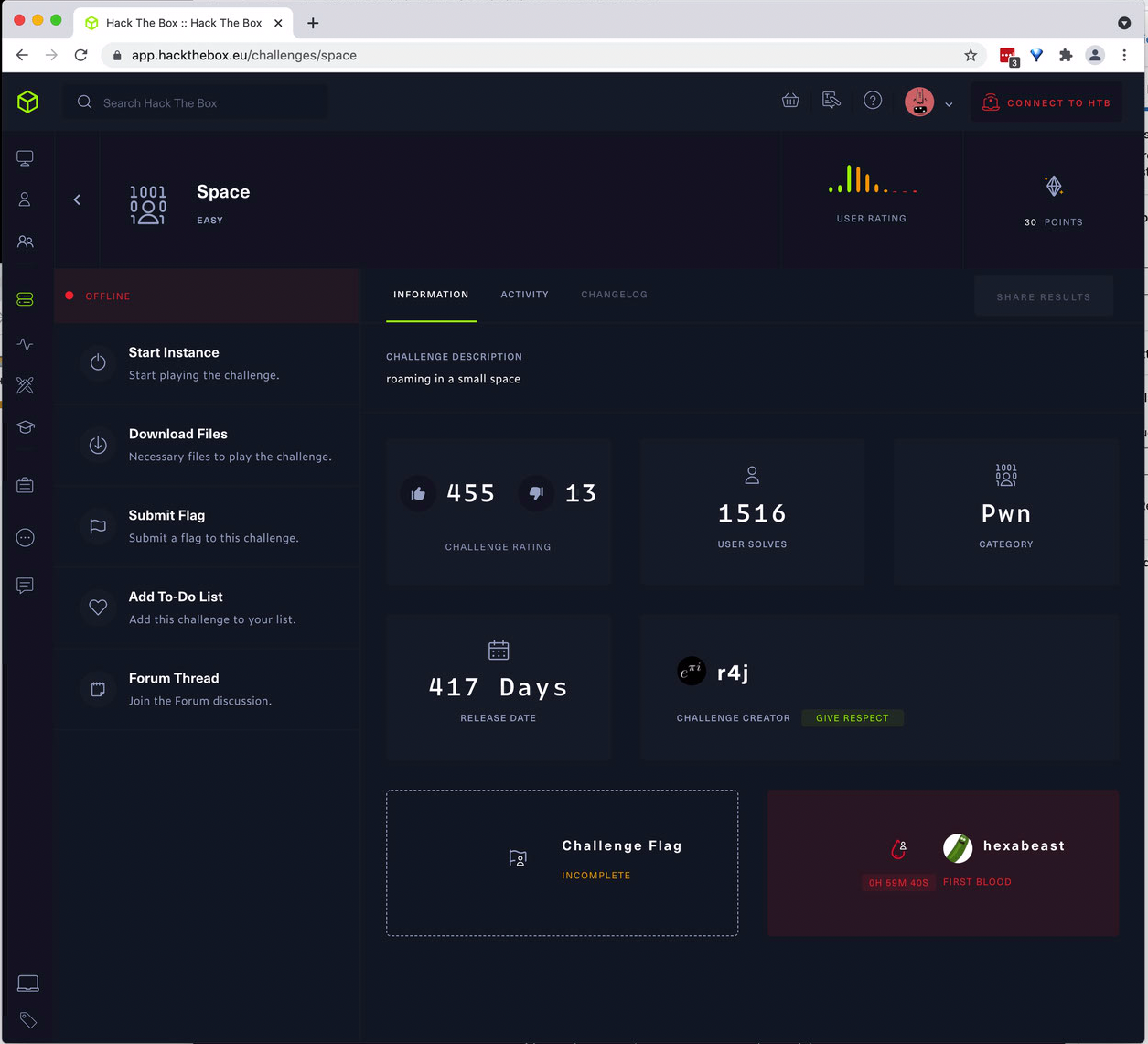
- Initial approach to a Challenge depends on its category:
- Some Challenges can be solved completely offline, using downloaded files provided on the challenge screen.
- Some Challenges require interaction with a vulnerable system online (much like Machines, but VPN access is not required for “active” Challenges).
- In some categories, notably Pwn and Web, a copy of the vulnerable program or website code is provided to you for analysis, and then you apply what you’ve discovered to the online instance.
- More information about playing Challenges can be found in the HtB Help Center.
- See Find The Flags below for information about what you’re looking for and what to do once you find it.
Find the Flags
- The object is to find the user and root flags on the machine you’ve chosen.
- The user flag is in a file called user.txt and is located in a user’s home directory / Documents folder, or otherwise accessible by the user you’re able to gain access as.
- The root flag is in a file called root.txt and is located in /root or similar location, and is accessible only by the root, Administrator, or equivalent user.
- For a Challenge, there will be a single flag, in the format HTB{th1s_is_th3_fl@g} unless otherwise specificed in the Challenge instructions.
- Once you have found a flag, go back to the machine detail page on HtB and click “Submit Flag” (on the left, below the machine name & IP address). Copy the flag itself and paste into the “Input Flag Hash” box in the popup that appears.
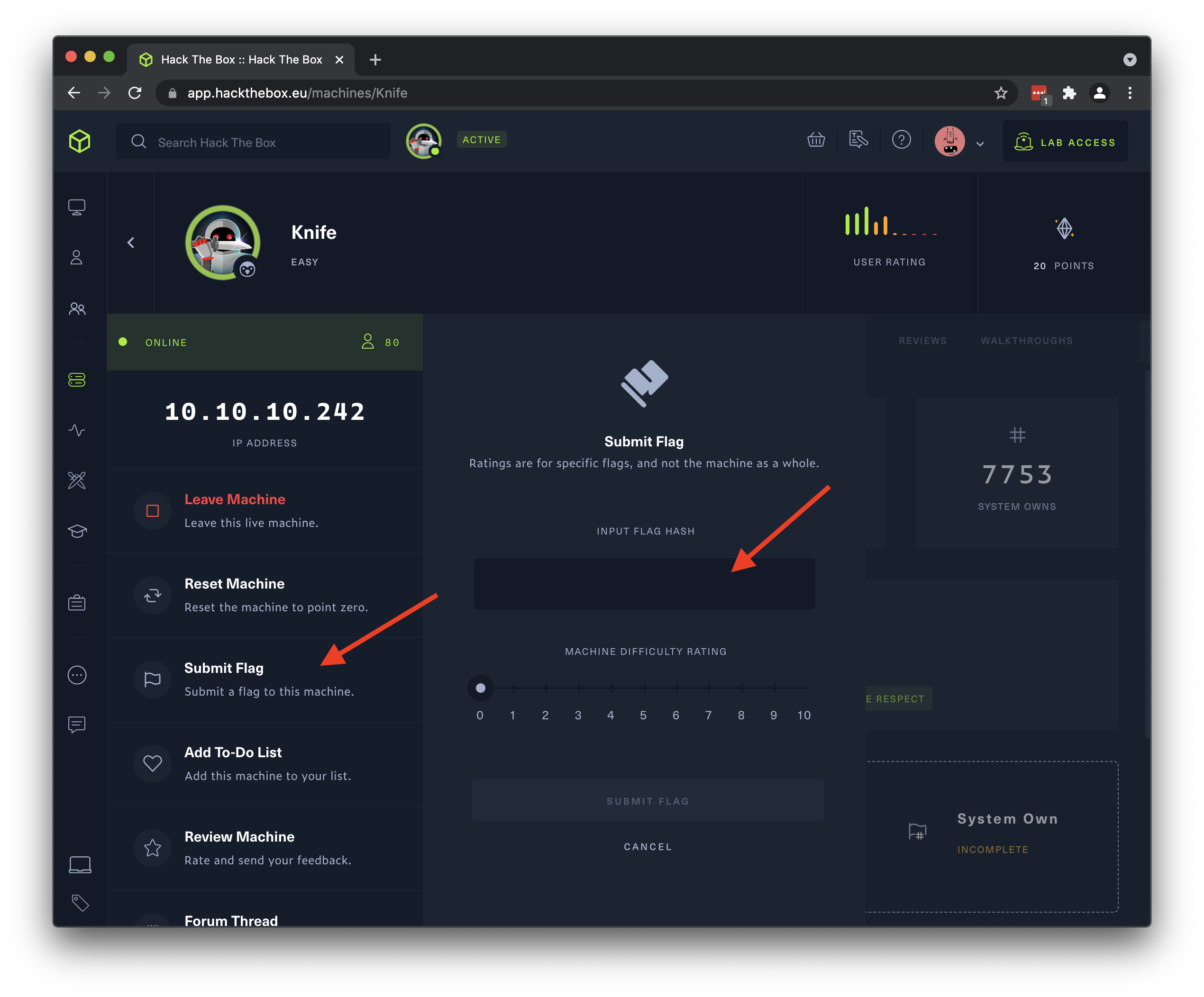
- If you suspect that a machine has been altered in such way as to block or change an exploit (it happens from time to time, accidentally, incidentally, or otherwise), use the “Reset Machine” button on the left, below the machine name & IP address, to revert the machine to its original state. If there are other users joined to the machine, they will have a chance to (temporarily) prevent the reset.
That’s all for now, happy hacking!